When it comes to SD-WAN, there are many different things to consider, such as whether you need to use virtualized infrastructure or hardware-based, the kind of security you are looking for, and how to reduce your overall attack surface. By understanding these things, you can make better decisions regarding your network.
Virtualized infrastructure vs. hardware-based infrastructure
Network Function Virtualization (NFV) is a software architecture that decouples network functions from proprietary hardware. It enables carriers and other service providers to deliver network services without purchasing expensive equipment. NFV also enhances flexibility and time to market for new services.
NFV can be implemented by using a content management platform, virtualized infrastructure, or a hypervisor. Hypervisors isolate network resources, enabling engineers to program and deploy virtual network components.
Software-defined networking enables organizations to distribute and allocate resources to accommodate changing demands dynamically. NFV provides hardware-independent, scalable, and flexible architecture that can easily support new services.
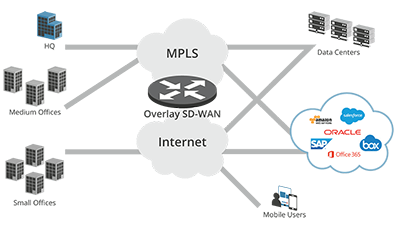
SD-WAN, or Software-Defined Wide-Area Networking, is a popular approach to implementing wide-area telecommunication networks. Using an open-standard-based approach, this solution offers strong security capabilities, scalability, and ease of deployment.
NFV is designed to enable wireless carriers and telecommunications service providers to improve their elasticity, agility, and time to market. Virtualization of network functions allows them to operate on less expensive, generic servers. The network functions can then be deployed on-demand, providing better performance. This centralized control reduces the burden on carrier networks and simplifies their management.
A key advantage of NFV is that it allows wireless carriers to repurpose their physical infrastructure. For example, a uCPE server can host virtual network functions.
Network administrators can easily adjust network operations and configure new functions by utilizing a centralized orchestration system. Changing business requirements or business scenarios can be addressed in minutes.
Cloud-first SD-WAN
Software-defined vast area network (SD-WAN) is an end-to-end virtual WAN architecture that is flexible and secure and provides a predictable, high-performance, and cost-effective solution for enterprise networks. It delivers networking services from a single point of control, making it easier to manage, scale and maintain.
For distributed employees, SD-WAN enables them to access cloud applications from multiple locations. In addition, it provides deep visibility into the network’s flows and allows IT to deploy and monitor applications effectively.
In order to provide the best user experience, a cloud-first SD-WAN architecture must support connectivity, reliability, security, and visibility. These are four key elements that enterprises need to consider when they choose a new SD-WAN solution.
Enterprises that are using cloud WAN connections face several reliability and performance issues. Because SD-WAN uses public internet, it can be susceptible to failure. Moreover, network managers must have the ability to prioritize traffic and configure SLAs for different applications.
A cloud-first SD-WAN architecture must also support micro-segmentation and reliability. While the architecture does not need to be perfect, it must be able to handle cloud traffic.
Cloud-first SD-WAN architecture also must support flexible billing and a consumption model that can adapt to changing business needs. This is important because applications have different performance requirements.
Lastly, network managers must have a management portal that can offer role-based administration. Policies must be designed to account for business needs and security requirements.
Security
SD-WAN architecture is a way to connect several locations to the internet securely. This technology allows organizations to manage their WANs from a central console, reducing costs and providing consistent application performance. With the ability to manage network security across all sites, SD-WAN increases operational efficiency and minimizes risk.
When choosing an SD-WAN provider, you should look for a vendor who offers service insertion and chaining. Both of these features allow you to add services without rebooting your WAN.
Another benefit of an SD-WAN solution is the ability to create virtual private networks. These networks are encrypted to help prevent data retransmission. This feature can be used to limit access to websites or restrict a user’s ability to view specific content.
Using the cloud can also help improve your network’s overall performance. Cloud services like Amazon Web Services can provide a secure connection to the public internet. The ubiquity of these services is growing, as experts predict a CAGR of 26.2% between now and 2028.
One of the key benefits of SD-WAN security is the ability to configure policies for real-time traffic. It is a good idea to look for a vendor that releases frequent updates.
Another way to keep your data safe is to use a firewall as a service. An SD-WAN that is integrated with a cloud service can allow you to take advantage of this capability.
Reducing the overall attack surface
SD-WAN has been one of the most rapidly adopted technologies in the past decade. It is often touted for its ability to simplify a WAN architecture, provide security, and enable businesses to implement defense-in-depth strategies more efficiently. This is due to the power of software-defined networking to leverage secure protocols and increased telemetry to improve network visibility and control.
Today, SD-WAN appliances can include UTM capabilities, protecting branch locations from cyberattacks. Organizations can identify potential weaknesses and take appropriate action with increased visibility into the overall attack surface. Ultimately, these measures reduce operational complexity and employee toil, leading to higher productivity and lower churn.
A large attack surface on a WAN can increase the risk of malware and other threats. Organizations can identify potential vulnerabilities and take appropriate actions by analyzing a WAN flow. Increasing visibility into the overall WAN can decrease the number of threat vectors and minimize the impact on on-premises networks if an attacker is successful.
Traditionally, IT teams have been limited by metrics from traditional routing protocols. However, advanced capabilities like Layer 7 visibility and fine-grained policy enforcement can significantly reduce the impact of network incursions. These capabilities can facilitate most minor privilege controls and ensure deny-by-default policies across the network.
Organizations should consider using an open-standard-based SD-WAN solution to manage the network effectively. Such solutions offer robust security features and the flexibility to configure and manage a WAN architecture in the most suitable way for each organization’s needs.